What is Splashtop?
Splashtop is a software solution that allows a user on one device (like a laptop or PC, a tablet or even a smartphone) to access another computer over a network, as if they’re sitting in front of it. You don’t need any additional hardware, and providing your computers, tablets and/or smartphones are reasonably recent, it’s a quick and easy process to get it running.
The technology is built by an established US company, founded in 2006, and now with over 30 million users worldwide.
How does Splashtop work?
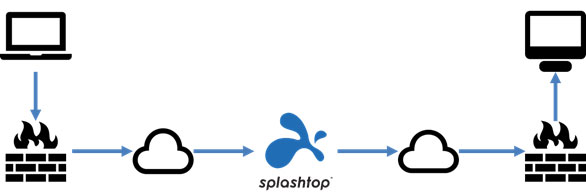
Usually the ‘remote access’ process takes place over an internet connection, where the user might be at home on a device (called the “client”: their own laptop, for example) and is accessing the desktop of another computer or server inside their organisation (called the “streamer”: their office PC, for example).
The user’s laptop essentially becomes a remote screen, keyboard and mouse controlling the PC inside the office.
A remote session initiated on a client device is routed over the internet to the Splashtop cloud service, and from there to the streamer device.
What devices does Splashtop work on?
For the streamer, Splashtop works on:
- Microsoft Windows (7, 8/8.1 and 10, and Server 2008, 2012, 2016 and 2019);
- Apple macOS (10.9 “Mavericks” and newer);
- Android (5.0 “Lollipop” and newer); and
- Linux (Ubuntu Desktop (16.04 and 1804), CentOS (7 and 8), Red Hat Enterprise Linux (7.3 to 8.1) and Fedora (29 to 31)).
For the client, Splashtop is compatible with:
- Microsoft Windows (7, 8/8.1 and 10)
- Apple macOS (10.9 “Mavericks” and newer)
- Android (5.0 “Lollipop” and newer); and
- Apple iOS (11 and newer).
For more information, see the Splashtop system requirements.
Is Splashtop secure?
Splashtop remote sessions are protected with TLS (version 1.2) and 256-bit AES ‘strong encryption’. This is broadly equivalent to the security level used in online banking.
TLS (Transport Layer Security) version 1.2 supports stronger hashing algorithms and encryption modes than TLS version 1.1, and is now generally considered the appropriate standard for secure browser-based applications.
AES (Advanced Encryption Standard) is the US government standard for data encryption and is the only publically accessible cipher approved by the NSA for use with ‘top secret’ information. At present there is no known conventional attack that can break 256-bit AES encryption.
Splashtop features
The Splashtop solution provides remote printing, supports multiple monitors, and allows easy file transfer (from the remote device to the business device, and vice versa), as well as quick and simple remote access, plus numerous other features:
- Remote printing: allows you to print files on the remote device to your local printer, so if you’ve got an important document at the office but you’re at home, you can print it on your home printer. For more information, have a look at the Splashtop remote printing page.
- Multi-monitor support: Splashtop supports viewing multiple displays from multiple displays: multi-to-one and multi-to-multi. Get more info at the Splashtop multi-monitor remote access page.
- File transfer: you can easily transfer files between your devices using the Splashtop remote access session. Splashtop supports several methods, including ‘drag and drop’ and ‘copy and paste’. There’s more information at the Splashtop file transfer page.
- Performance: in internal lab tests, Splashtop reached up to 60 frames per second (fps) in 1080P (HD) resolution and up to 30 fps in 4K resolution for Windows. Find out more at the Splashtop high-performance remote access page.
- Remote reboot: a remote Windows or Mac device can be rebooted from the Splashtop app or web console. Find out more at the Splashtop remote reboot page.
- Session recording: the Session Recording function can be used to record remote access sessions, and save them to the local device. There’s a guide to this on the Splashtop session recording page.
- Two users: providing there are enough licences, two users can remotely access one computer at the same time. See the Splashtop support article about more than one connection to the same computer for more details.
Think IT and Splashtop
Think IT have partnered with Splashtop, which means we have access to the best pricing, as well as being able to provide deployment (i.e. installation and configuration) services for clients, and support and maintenance. If we’re unable to resolve an issue, we also have access to Splashtop support and can raise any issues with them on your behalf.
For deployment, the standard ‘streamer’ application can be downloaded and accessed by providing the Splashtop ID and password through the ‘client’. Alternatively, we can create a customised deployment streamer app that automatically binds to a Splashtop account.
Alternatives to Splashtop
There are other products available that are similar to Splashtop, in that they don’t require any additional hardware, and either use a browser or an app to make the remote connection with their service which then connects to the target device:
- Products like LogMeIn, GoToMyPC, TeamViewer and AnyDesk are alternatives to Splashtop as remote desktop access tools.
- Products like ConnectWise Control, Zoho Assist and VNC Connect do support remote desktop access, but are designed primarily for remote technical support.
We have evaluated a lot of them in the process of selecting Splashtop as the remote desktop access solution for our clients. In most cases we have found these alternatives to be more costly than Splashtop, and/or to omit certain features we think are important.
RDP (Remote Desktop Protocol), developed by Microsoft, is also commonly used for remote desktop access. Windows desktop operating systems (like Windows 10) include a built-in ‘native’ RDP client, and Windows Server operating systems include a built-in RDP server. The Microsoft Remote Desktop client is also available on the App Store for macOS X users.
However, whilst RDP is functional there have been numerous exploits demonstrating vulnerabilities in its standard security, and adding additional security, though possible, can be complex and expensive. As a result many organisations now prefer solutions like Splashtop that are cost effective and are more secure ‘out of the box’.
For more information, check out Insights guide to secure remote access with RDP.
If you want to discuss remote access or RDP, want to find out more about Splashtop, or need some assistance with any of these recommendations, just get in touch with us.
Glossary
| AES | or Advanced Encryption Standard is an encryption specification set out by NIST (the US National Institute of Standards and Technology) and has become the industry standard for data security. |
| Cipher | means an algorithm (or set of steps that a computer will perform) that can be applied to data to encrypt it, or to encrypted data to decrypt it. |
| Encrypting | or encryption is the process of converting original data (called “plaintext”) into data that cannot easily be read or used (called “ciphertext”) without authorisation (i.e. without having the Key). |
| Exploit | occurs when a vulnerability is taken advantage of by an attacker. |
| Key | in cyber security terms is the secret piece of data that, when paired with the Cipher, makes the encrypted data secure; without the key, it is very difficult (with strong encryption) to decipher the encrypted data. |
| Strong encryption | is an encryption method using a very large cryptographic key. Larger keys take longer to break. 256 bit encryption is considered strong encryption. |
| Threat agent | is a person (or a process) that exploits a vulnerability. Examples include employees not following procedure, or a hacker. |
| TLS | or Transport Layer Security is a communication protocol allowing communication between a client (e.g. a web browser) and a server (e.g. a web server) to be secured. |
| Vulnerability | is a weakness that allows a threat to compromise it. Examples include a wireless access point with no security, firewall ports open, or no door locks. |





