What is RDP?
RDP is a technology developed by Microsoft that allows a user on one computer to access the desktop of another computer over a network.
Usually this access takes place over an internet connection, where the user might be at home on a device (their own laptop, for example) and is accessing the desktop of another computer or server inside the organisation (their office PC, for example). The user’s laptop essentially becomes a remote screen, keyboard and mouse controlling the PC inside the office.
Microsoft Windows desktop operating systems (like Windows 10) include a built-in ‘native’ client for this, and Windows Server operating systems include a built-in RDP server. The Microsoft Remote Desktop client is also available on the App Store for macOS users.
Is RDP secure?
RDP supports strong encryption, and by default RDP sessions do use encryption (though the encryption level can vary depending on the client devices in use).
However, there have been numerous exploits demonstrating vulnerabilities in RDP, so additional security controls are important.
Some examples of RDP vulnerabilities that have been exploited include the Remote Code Execution vulnerability (does not require user authentication or interaction to run, and allows an attacker to execute remote code), and the CredSSP vulnerability (allows an attacker to exploit part of the RDP authentication process to execute remote commands).
More importantly, RDP requires various additional steps to address a range of weaknesses and achieve and maintain a good standard of security. This is detailed in sections 4 and 5.
Alternatives to RDP
Whilst RDP is functional and can be secured (as set out in the guidance below), many organisations now seek straightforward, low-cost solutions that are more secure ‘out of the box’.
These alternatives usually don’t require any additional hardware within the business or at the remote access end, and either use a browser or an app to make the remote connection with their service, which then connects to the target device.
For security, we recommend the use of the TLS protocol (version 1.2 or higher) and AES encryption (which supports encryption keys of at least 128 bits) in the communications with the service.
Think IT can provide the Splashtop service: a cloud-based remote desktop access solution for secure access to business PCs and servers from Windows, macOS, Android or iOS devices, anywhere.
The Splashtop solution provides remote printing, supports multiple monitors, and allows easy file transfer (from the remote device to the business device, and vice versa), as well as quick and simple (and secure) remote access, plus numerous other features. For most clients, it is also very good value for money when compared to alternatives like LogMeIn, GoToMyPC or TeamViewer.
For more information, just get in touch with us or have a look at our Insights guide to secure remote access using Splashtop.
How RDP works
Below is a simplified example to illustrate how an RDP session is created.
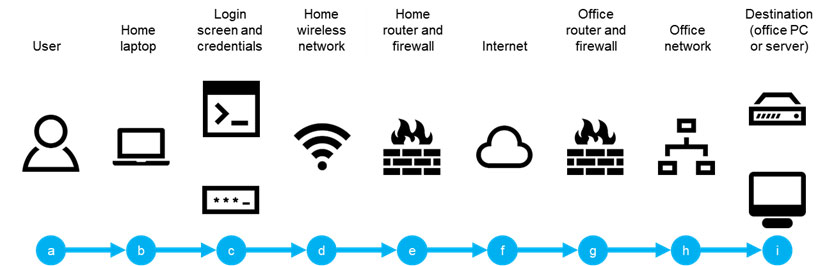
In this example, a user is using RDP to remotely access a PC or server in their office.
The RDP session begins with the user (a), using their laptop at home (b). This could be their personal laptop, or a work laptop. For the purposes of the example, it is a Windows 10 laptop.
The user launches an RDP session from their laptop, and is presented with the login screen, and they provide their username and password (c). Assuming the correct username and password have been provided, the process continues to connect the RDP session.
As the user is at home, this traffic is carried over their wireless network (d) to their home router, which we assume also has a firewall (e).
The firewall performs various normal security duties, and the router directs the traffic to the user’s internet service provider (ISP).
The ISP routes the traffic across the internet (f), where the office ISP picks it up, and routes the traffic to the office.
The office also has a router and a firewall (g). Again, the firewall performs its security duties, and routes the traffic to the office local network (h).
The office local network then routes the traffic to the destination PC or server (i) that the user is accessing remotely, and the session is created.
The user now has remote access to the PC or server.
RDP weaknesses
However, there are numerous security vulnerabilities in this process. Using the same example, some of the vulnerabilities are highlighted below.
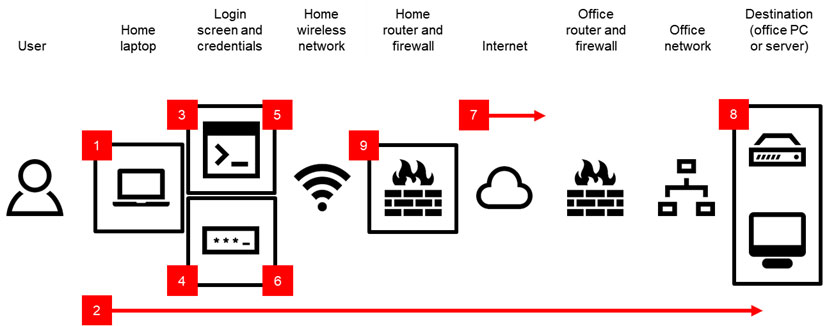
- The user’s laptop may not have the latest updates (e.g. Microsoft found critical vulnerabilities in August 2019 that required updates).
- The user’s connection over the internet to the office is ‘open’. This means attackers can detect the type of traffic being passed.
- An attacker can identify the RDP service running at the office, by observing the user’s traffic or by scanning the open ‘ports’ at the office, and can attempt to access the PC or server via RDP.
- If the user’s password is poor, the attacker may be able to gain access (e.g. by attempting use of common passwords or by guessing the user’s password from details on their social media profiles).
- The attacker can attempt to use as many different passwords as they choose; if the password fails, the system will return them to the login screen to try again.
- There are no additional authentication steps other than the password, so the attacker can continue trying to find a working password.
- The user’s open connection is also transmitted in ‘plaintext’ (no encryption): an attacker can intercept and read the traffic.
- The RDP server is set to allow RDP sessions from all users in the company. This means that even if the user in this example has a strong password, the attacker can attempt to find another user with a weaker password, or launch a ‘social engineering’ attack against all users in the company to attempt to obtain passwords.
- The RDP server is set to allow RDP sessions from any IP address. This means that the attacker doesn’t need to compromise the user’s wireless network in order to attempt an RDP connection; they can do it from anywhere.
Addressing RDP weaknesses
There are, however, effective steps that can be taken to mitigate these vulnerabilities.
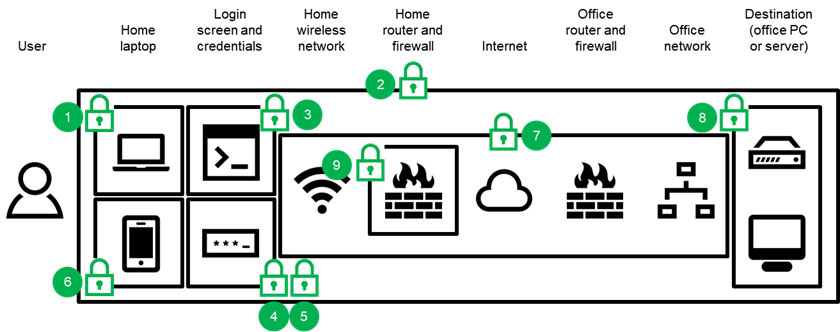
- The user’s computer can be maintained with the latest updates, preventing attacks that exploit ‘patched’ vulnerabilities.
- The user’s connection over the internet to the office can be secured with a virtual private network, preventing traffic from being detected.
- The RDP server can be configured to keep the RDP session closed until the correct password has been provided, preventing attacks that seek to overload the RDS server.
- The user’s password can be changed to a stronger password, preventing certain types of password-guessing attacks.
- The RDP server can be configured to lockout the user’s RDP access if too many incorrect passwords are entered, preventing the attacker from being able to continue to try passwords indefinitely.
- Additional authentication steps can be added, requiring the attacker to not only obtain the correct password, but also the extra element (e.g. a code sent to the user’s phone by the system).
- The RDS server can require the traffic to be encrypted, preventing RDP sessions that can be intercepted by attackers.
- The RDS server can be configured to only allow sessions for pre-agreed users, preventing attackers using any user’s credentials.
- The RDP server can also be configured to only allow sessions from pre-set IP addresses, preventing attackers from making RDP connections from other locations.
RDP security steps
For organisations that need to continue to use RDP, or are considering using it, the following ten key security steps are recommended.
| 1 | Update software | Keeping software updated is a recommended security step in numerous contexts, and it is entirely relevant to RDP.
The Microsoft patch cycle can benefit organisations using RDP by updating components as part of the Microsoft Updates process (as opposed to third-party software that may require separate updating). The key is to ensure updates are installed regularly. It is recommended to run Windows Update as often as possible – a weekly check process is a good idea. Think IT are able to help clients ensure Windows Updates are performed frequently and when required. |
| 2 | Use a VPN | More often than not, once RDP is configured it will be available to users over any Internet connection (i.e. the open Internet).
Attackers will commonly scan networks for open RDP ‘ports’, and even with security measures in place, ‘denial of service’ or ‘account lockout’ attacks can be performed which make the RDP service fail. It is recommended to only allow RDP access over a VPN. This means not allowing RDP to run externally through the organisation’s firewall, but connecting remote VPN users to the organisation’s local network and then to open RDP sessions with local devices when a VPN session is successfully established. Note that this will prevent users from using RDP on devices that don’t support the VPN or do not have it configured. Think IT are able to provide and configure VPNs for clients, using a hardware or software-based approach. |
| 3 | Use Network Level Authentication (NLA) | An RDP user needs to provide their username and password in order to access the target computer. NLA requires the connecting user to authenticate before an RDP session is established with the receiving computer (e.g. PC in the office), whereas without NLA the login screen is presented, increasing the attack surface for ‘denial of service’ and ‘brute-force’ attacks.
NLA is usually enabled by default on Windows 8 and newer desktop, and Windows Server 2012 and newer server operating systems. Organisations should consider checking the ‘Require user authentication for remote connections by using Network Level Authentication’ Group Policy setting. Think IT are able to configure this policy for clients with managed servers. |
| 4 | Password strength | Good passwords (i.e. ‘strong and long’) will help to ensure that brute-force attacks are more difficult for attackers. The key elements in a strong password are:
Organisations should consider setting the ‘Password must meet complexity requirements’ within Group Policy for RDP users. Think IT are able to provide password guidance and can also configure this policy for clients with managed servers. Check our Insights Password Guide for more information. |
| 5 | Set account lockout | Without certain settings, a user (or an attacker) is able to continue to try passwords (or, in the case of the attacker, use a computer to do so) in an attempt to eventually gain access; the system will simply continue to reject incorrect passwords and present the user/attacker with the same screen to attempt access again (and again, and again).
By setting account lockout, a user account will be locked automatically after a certain number of incorrect password attempts have been made (e.g. ten incorrect attempts). This will help to ensure that brute-force attacks are more difficult for attackers. Organisations should consider setting the ‘Account Lockout Policy’ within Group Policy for RDP users. Think IT are able to configure this policy for clients with managed servers. |
| 6 | Implement multi factor authentication (MFA) | Multi factor authentication involves adding at least one more authentication factor to the normal ‘username and password’ (being ‘something you know’), where the additional factors are either ‘something you have’ (like a ‘one-time-password’ sent in an SMS message) or ‘something you are’ (like a fingerprint).
This is the technology many online banks use as part of the ‘authentication’ process: as well as a username and password, it may be necessary to provide a code that is sent by text message or by using a card reader. Adding multi factor authentication typically involves the use of a third party service. Think IT are able to provide multi factor authentication using the Duo Security (now part of Cisco) solution. |
| 7 | Configure RDP to use TLS | TLS is a way of securing traffic sent over the Internet. It doesn’t secure data on computers, but instead encrypts data ‘in transit’ so that attackers are unable to read it.
Implementing TLS can help to reduce the risk of ‘man-in-the-middle’ attacks. TLS support is enabled by default in Windows Server 2012 and newer server operating systems. Though support was added for Windows Server 2008 R2, organisations should no longer be using this version as Microsoft ceased support in January 2020. To complete TLS implementation, an organisation will need to obtain a certificate from a Certificate Authority (CA). Think IT are able to provide certificates from the Comodo CA (also called Sectigo), one of the largest CAs in the world. |
| 8 | Enable RDP on an ‘as-needed’ basis | Depending on how user accounts are set up in an organisation, it may be the case that everyone has RDP access, but in practice that not everyone needs it.
By limiting the number of users that can access computers via RDP the organisation can reduce the likelihood of exploitation. By default RDP is enabled for users in the ‘Administrators’ group, however if an alternative remote system administration tool is used, it is recommended that Administrator RDP access is removed. Additionally if there are other users that do not require RDP access, that access should also be removed. Organisations should consider setting the ‘Allow log on through Remote Desktop Services’ within Group Policy for RDP users, and adding only required users to the ‘Remote Desktop Users’ group. Think IT are able to configure this policy for clients with managed servers. |
| 9 | Restrict access to certain IP addresses | Again, it is more often the case that RDP is set up to allow users to access it from any IP address. Should a user’s username and password be compromised (and where no multi factor authentication is in place), an attacker would be able to connect remotely to the organisation’s internal device(s).
The Windows Firewall can be configured with an Inbound Rule to only allow RDP connections from pre-defined IP addresses. Note that this will prevent users from using RDP from IP addresses that have not been added to the firewall rule. Think IT are able to configure these firewall rules for clients with managed servers. |
| 10 | Implement a robust data backup plan | Another common piece of security advice that is generally applicable to using RDP: make sure all important data is backed up.
If the security steps above fail, one of the most important elements in recovering from whatever disaster occurs is a reliable backup that can be used to efficiently restore data. The key elements in a robust backup plan are:
Think IT are able to provide backup solutions and services, including both cloud backup and on premises (e.g. USB hard disk) backup. |
If you want to discuss remote access or RDP, or need some assistance with any of these recommendations, just get in touch with us.
Glossary
| Advanced Encryption Standard | or AES is an encryption specification set out by NIST (the US National Institute of Standards and Technology) and has become the industry standard for data security. |
| Authentication | is the means of verifying that a person (i.e. a user) is who they claim to be (e.g. by requiring the correct password to be provided with the corresponding user name). |
| Authentication factor | is a category of authentication, where categories include ‘something you know’ (e.g. a password); ‘something you have’ (e.g. a smartcard); or ‘something you are’ (e.g. a fingerprint). |
| Brute-force attack | involves an attacker attempting many passwords with the intention of eventually finding the correct one. |
| CA | or ‘Certificate Authority’ is an organisation that issues digital certificates. |
| Certificate | is an electronic document that proves a person, organisation or computer system actually is who or what they say they are. |
| Denial of service attack | or ‘DoS’ attack is a type of attack in which the attacker overloads a system to disrupt normal operation. |
| Encrypting | or encryption is the process of converting plaintext into data that cannot easily be read or used (called “ciphertext”). |
| Exploit | occurs when a vulnerability is taken advantage of by an attacker. |
| Group Policy | is a set of controls within Windows Server operating systems allowing administrators to define what users can and cannot do. |
| IP address | or ‘Internet Protocol address’ is the number that uniquely identifies a computer to other computers and networks. |
| Man-in-the-Middle attack | or ‘MitM’ attack occurs when an attacker is positioned between one computer and another, intercepting the communications between them whilst they believe they are communicating directly with each other. |
| Open connection | is a simple connection between two points (e.g. a user’s home and their office), without authentication or encryption. |
| Patch | or ‘update’, ‘hotfix’ or ‘bugfix’ is a software change to a system (e.g. Windows 10) to correct a defect or improve functionality. Patches often address vulnerabilities. |
| Plaintext | is original unencrypted data before encryption is performed, originally so called as it was human-readable. |
| Port | is a communication point for a specific process or service, allowing one system to communicate with another for that specific purpose. The standard port for RDP is 3389. |
| Ransomware | is a form of malware that enables criminals to encrypt or lock data or devices remotely and demand payment (the ransom) for their release. |
| Security control | is a counter-measure (or safeguard) put in place to mitigate the likelihood that a threat agent will exploit a vulnerability. |
| Strong encryption | is an encryption method using a very large cryptographic key. Larger keys take longer to break. 256 bit encryption is considered strong encryption. |
| Threat agent | is a person (or a process) that exploits a vulnerability. Examples include employees not following procedure, or a hacker. |
| TLS | or Transport Layer Security is a communication protocol allowing communication between a client (e.g. a web browser) and a server (e.g. a web server) to be secured. |
| Virtual Private Network | or ‘VPN’ creates an authenticated (and usually encrypted) ‘tunnel’ between two points (e.g. a user’s home and their office), protecting both points from various attacks and making it much more difficult to intercept the data sent between them. |
| Vulnerability | is a weakness that allows a threat to compromise it. Examples include a wireless access point with no security, firewall ports open, or no physical door locks. |





